
If your company has not been compromised yet, it is only a matter of time. ITnGen maintains an up to date awareness of current cybersecurity risks, prevalence, correlate these concerns to your environment to understand if your company is at risk and prioritize threats. ITnGen understands if you are reacting to cybersecurity threats, it is already too late. ITnGen performs detailed Pen Test analysis, to ensure all controls and guardrails are in place protecting companies from risk of compromise.
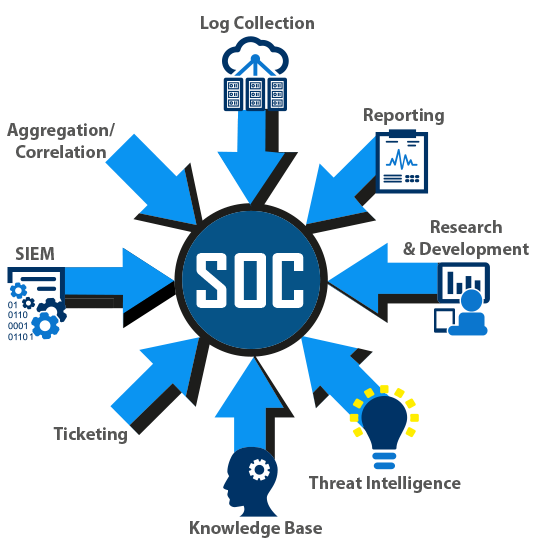
ITnGen works with your existing IT, Legal, and GRC teams to quickly come to speed on existing security and compliance challenges. ITnGen develops and automates custom SOC solutions addressing your company’s needs integrating SIEM capabilities such as log collecting, monitoring, alerting, reporting, proactive threat detection, forensics investigation, prioritization, and routine maintenance.
ITnGen creates run books, SOPs, guidelines or security policies ensuring regulatory compliance is achieved while implementing a repeatable process creating the foundation of your secure environment. Cybersecurity is a constant cycle of auditing the entire environment, including software, data classification and workflows, asset inventory, user management and access controls, understanding all operational processes, and the ability to detect anomalies, intrusion, deviation, threats and non compliance.
12 Defensive Layers of Security
- Firewalls and other access controls
- Intrusion detection technologies (IDS)
- Endpoint Detection and Response (EDR)
- Managed Detection and Response (MDR)
- Email security gateway
- Vulnerability Management
- Next-generation antivirus (NGAV)
- Data encryption and authentication mechanisms
- Intrusion prevention systems (IPS)
- Data loss prevention (DLP) solutions
- Centralized Identity and Access Management (CIAM)
- Logging and automated alerting
Regulatory Compliance & Cyber Security Frameworks
ITnGen security experts help companies meet regulatory compliance requirements such as ISO, HIPAA, PCI-DSS, SOC2, SOX, GDPR, etc.
ITnGen understands many different Cyber Security Frameworks (CSF) such as NIST, CISA, OWASP, MITRE etc. These frameworks provide logical controls for organizations to align with ensuring maximum security and privacy.
NIST
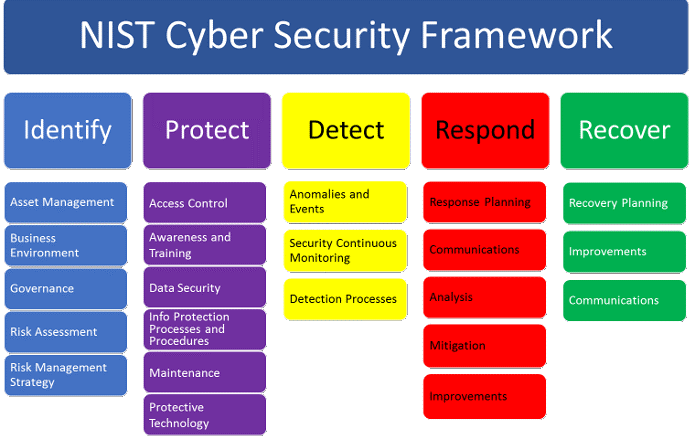
NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies and the broader public. Our activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in technologies and future challenges.
NIST contributes on cryptography, education and workforce, emerging technologies, risk management, identity and access management, measurements, privacy, trustworthy networks and trustworthy platforms. NIST also provides the NVD – National Vulnerability Database.
https://www.nist.gov/cyberframework/online-learning/components-framework
CISA
Relationship to the Cybersecurity Framework

CISA helps organizations use the Cybersecurity Framework to improve cyber resilience. While the CRR predates the establishment of the Cybersecurity Framework, the inherent principles and recommended practices within the CRR align closely with the central tenets of the Cybersecurity Framework. The CRR enables an organization to assess its capabilities relative to the Cybersecurity Framework and a crosswalk document that maps the CRR to the NIST Framework is included as a component of the CRR Self-Assessment Package. Though the CRR can be used to assess an organization’s capabilities, the Framework is based on a different underlying framework and as a result an organization’s self-assessment of CRR practices and capabilities may fall short of or exceed corresponding practices and capabilities in the Framework. A mapping of the CRR to the Cybersecurity Framework is available here: CRR NIST Framework Crosswalk.
Development of the CRR
The Department of Homeland Security (DHS) partnered with the Computer Emergency Response Team (CERT) Division of Carnegie Mellon University’s Software Engineering Institute to create the CRR. The CRR is a derivative of the CERT Resilience Management Model (RMM) (http://cert.org/resilience/rmm.html) tailored to the needs of critical infrastructure owners and operators.
Ten Domains
One of the foundational principles of the CRR is that an organization deploys its assets (people, information, technology, and facilities) in support of specific operational missions or critical services. Applying this principle, the CRR seeks to understand an organization’s capabilities in performing, planning, managing, measuring, and defining operational resilience practices and behaviors through an examination of the following ten domains:
- Asset Management
- Controls Management
- Configuration and Change Management
- Vulnerability Management
- Incident Management
- Service Continuity Management
- Risk Management
- External Dependency Management
- Training and Awareness
- Situational Awareness
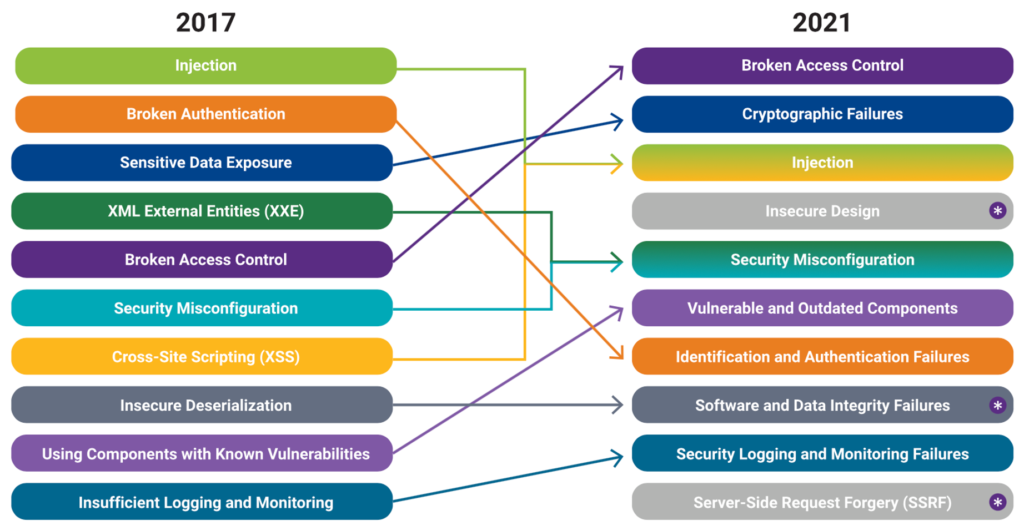
OWASP 10

The Open Web Application Security Project (OWASP) is a nonprofit foundation dedicated to improving software security. It operates under an “open community” model, which means that anyone can participate in and contribute to OWASP-related online chats, projects, and more. For everything from online tools and videos to forums and events, the OWASP ensures that its offerings remain free and easily accessible through its website.
The OWASP Top 10 provides rankings of—and remediation guidance for—the top 10 most critical web application security risks. Leveraging the extensive knowledge and experience of the OWASP’s open community contributors, the report is based on a consensus among security experts from around the world. Risks are ranked according to the frequency of discovered security defects, the severity of the uncovered vulnerabilities, and the magnitude of their potential impacts. The purpose of the report is to offer developers and web application security professionals insight into the most prevalent security risks so that they may fold the report’s findings and recommendations into their own security practices, thereby minimizing the presence of known risks in their applications.
MITRE ATT&CK

MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
With the creation of ATT&CK, MITRE is fulfilling its mission to solve problems for a safer world — by bringing communities together to develop more effective cybersecurity. ATT&CK is open and available to any person or organization for use at no charge.
CIS v8
The CIS Critical Security Controls (CIS Controls) are a prioritized set of Safeguards to mitigate the most prevalent cyber-attacks against systems and networks. They are mapped to and referenced by multiple legal, regulatory, and policy frameworks. CIS Controls v8 has been enhanced to keep up with modern systems and software. Movement to cloud-based computing, virtualization, mobility, outsourcing, Work-from-Home, and changing attacker tactics prompted the update and supports an enterprise’s security as they move to both fully cloud and hybrid environments.